Objective
- Mac Address Filtering Hackensack
- Mac Address Filtering Hack Account
- Mac Address Filtering Security
- Mac Address Filtering Check Epson Printer
MAC spoofing is a technique for changing a factory-assigned Media Access Control (MAC) address of a network interface on a networked device. The MAC address that is hard-coded on a network interface controller (NIC) cannot be changed. However, many drivers allow the MAC address to be changed. Additionally, there are tools which can make an operating system believe that the NIC has the MAC. Jul 13, 2020 MAC filtering, or MAC white- or blacklisting, is often used as a security measure to prevent non-whitelisted or blacklisted MAC addresses from connecting to the wireless network. MAC Address stands for media access control address and is a unique identifier assigned to your network interface. MAC addresses are used as a network address for most IEEE 802 network technologies, including Ethernet and WiFi. Logically, MAC addresses are used in the media access control protocol sublayer of the OSI reference model. Hackers will just spoof the mac address to retain there anonymity. There never use original mac address and IP address. Jul 14, 2020 You can hack mac filtering wifi easily by changing your mac address. This is the first tutorial. In the last tutorial i will show you how you can hack mac filtering wifi without root. How To Bypass Mac filtering of Any Wifi Router 100 Working for MAC OS X and iOS. This tool will work on your Mac, all latest versions are supported. Our tool is reliable and will do exactly what you expect and more. How To Bypass Mac filtering of Any Wifi Router 100 Working will not only work on MAC but it will work on WINDOWS 10 AND 7 and iOS.
 Spoof a MAC address to gain access to MAC whitelisted network.
Spoof a MAC address to gain access to MAC whitelisted network.Distributions
It's recommended that you use Kali Linux, but you can install the required programs on any distribution.Requirements
A working Linux install with root privileges and a wireless adapter. You should also have a router that you can set up with a MAC whitelist to test.Difficulty
EasyConventions
- # - requires given linux commands to be executed with root privileges either directly as a root user or by use of
sudocommand - $ - requires given linux commands to be executed as a regular non-privileged user
Introduction
Mac Address Filtering Hackensack
MAC address whitelisting sounds like a great way to prevent unauthorized access to your wireless network, but it doesn't work. The purpose of this guide is to demonstrate exactly how easy it is to spoof a whitelisted MAC address and gain access to a restricted network.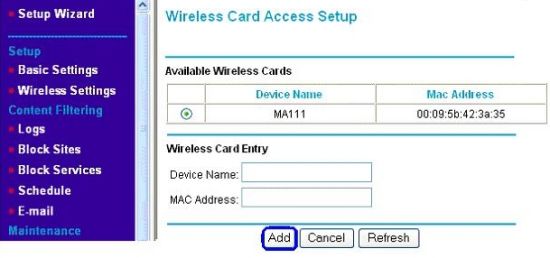
This guide is purely for educational purposes. DO NOT attempt this on a network that you do not own.
Install Aircrack-ng and Macchanger
If you're using Kali, don't worry about this part. You already have what you need. If you're on a different distribution, you need to installaircrack-ngMac Address Filtering Hack Account
and, if you'd prefer it toip, macchanger. Chances are, they're both readily available in your distro's repos, so install them.Find A Valid MAC Address
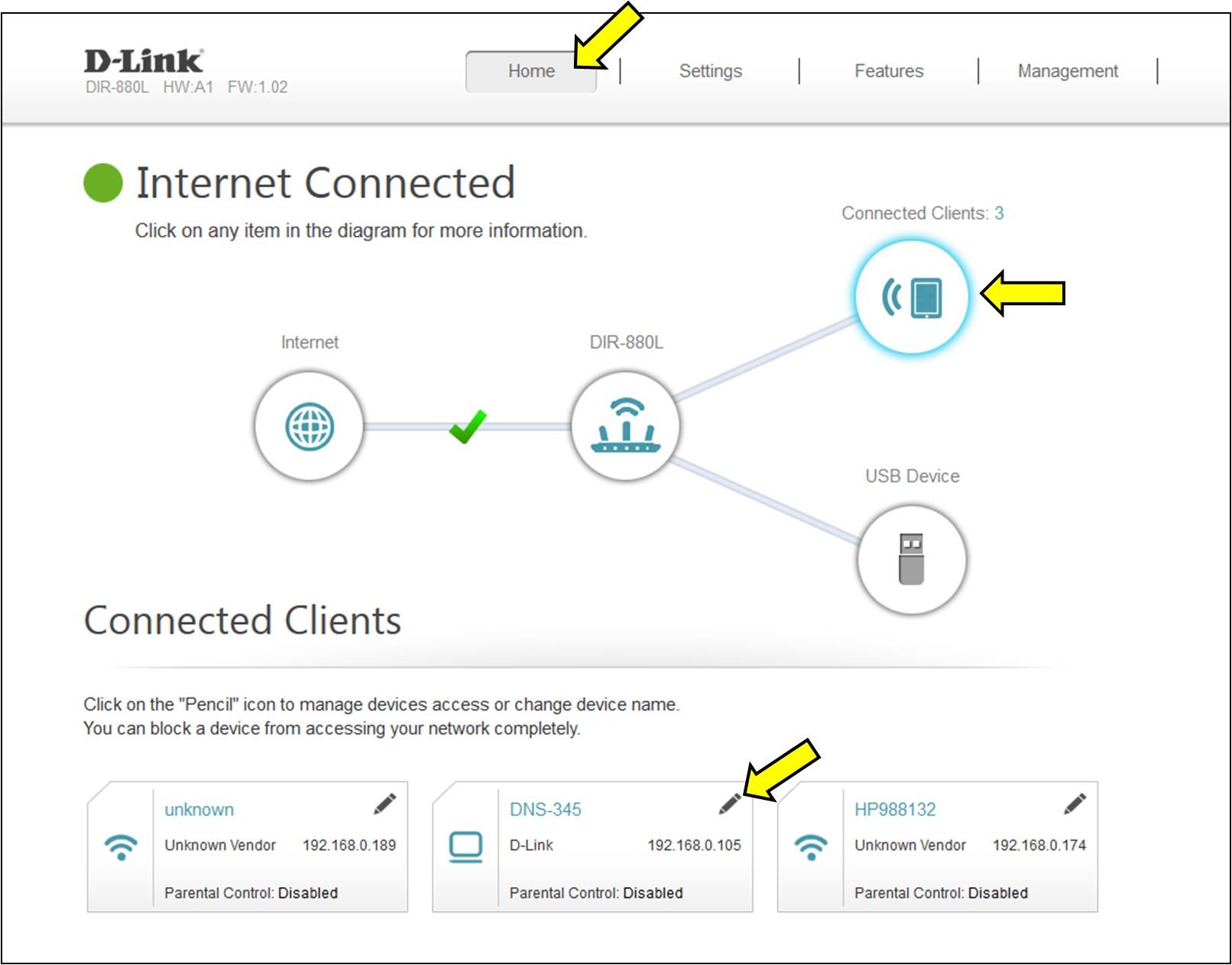
Before you spoof a MAC address, you need one to duplicate. Assuming that only whitelisted addresses can access the network, you need to find the MAC address of a connected device. The best way to do this is by listening to traffic with Aircrack.Run
ip a to find the interface of your wireless interface. When you have it, use Aircrack to create a new virtual monitoring interface.Take a look at the message in the terminal. It contains the name of the virtual interface. It's usually mon0..You'll see a table of date about the wireless networks in your area. Find the one that you're trying to connect to, and note the BSSID and channel. When you have them, cancel that command.Rerun
airodump-ng, specifying the BSSID and channel. This will narrow your results and make the clients easier to pick out.At the bottom of these new results, you'll see a second table. That table contains information about client connections. To the right, you'll see the MAC address of the network followed by the MAC of client. Pick one, and notate it. That's what you'll be spoofing.